

You work hard for your money. We're working hard to keep it safe!
The term 'information security' means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide integrity, confidentiality, and availability.
- Your Account Number
- Username or Password
- Your SSN
- You PIN
- Your Birthday
- Your Address
- Share a One-Time Code
- Reveal a Security Question
Note: You may be asked to verify confidential information if you call us, but rarely the other way around. If you’re ever in doubt that a bank call is legitimate, hang up and call the bank directly. If a caller pressures you to stay on the line and provide bank information right away or something bad will happen, it is a scam. Hang-up and call your bank to talk to a real bank employee.
- Social engineering is the attempt to manipulate or trick a person into providing confidential information to an individual that is not authorized to receive such information.
- Pretexting
- An invented scenario is used to engage a potential victim to try and increase the chance that the victim will bite. It's a false motive usually involving some real knowledge of the victim (e.g. date of birth, Social Security number, etc.) in an attempt to get even more information.
- Phishing
- The process of attempting to acquire sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity using bulk email which tries to evade spam filters. Emails claiming to be from popular social websites, banks, auction sites, or IT administrators are commonly used to lure the unsuspecting public. It’s a form of criminally fraudulent social engineering.
- Spear Phishing
- A small, focused, targeted attack via email on a particular person or organization with the goal to penetrate their defenses. The spear phishing attack is done after research on the target and has a specific personalized component designed to make the target do something against their own interest. Here is more about how they do it.
- Water-Holing
- This technique takes advantage of websites people regularly visit and trust. The attacker will gather information about a targeted group of individuals to find out what those websites are, then test those websites for vulnerabilities. Over time, one or more members of the targeted group will get infected and the attacker can gain access to the secure system.
- Quid Pro Quo
- Latin for 'something for something', in this case it's a benefit to the victim in exchange for information. A good example is hackers pretending to be IT support. They will call everyone they can find at a company to say they have a quick fix and "you just need to disable your AV". Anyone that falls for it gets malware like ransomware installed on their machine.
- Honeytrap
- A trick that makes men interact with a fictitious attractive female online. From old spy tactics where a real female was used.
- Diversion Theft
- A 'con' exercised by professional thieves, usually targeted at a transport or courier company. The objective is to trick the company into making the delivery somewhere other than the intended location.
- Baiting
- Baiting means dangling something in front of a victim so that they take action. It can be through a peer-to-peer or social networking site in the form of an explicit movie download or it can be a USB drive labeled “Q1 Layoff Plan” left out in a public place for the victim to find. Once the device is used or malicious file is downloaded, the victim’s computer is infected allowing the criminal to take over the network.
- Tailgating
- A method used by social engineers to gain access to a building or other protected area. A tailgater waits for an authorized user to open and pass through a secure entry and then follows right behind.
- Scareware
- Also deception software, rogue scanner software, or fraud ware, scareware, is a form of computer malware that deceives or misleads users into paying for the fake or simulated removal of malware. Scareware, in recent years, has become a growing and serious security threat in desktop computing.
Spotting and Avoiding Tech Support Scams
Tech support scammers use many different tactics to trick people. Spotting these tactics will help you avoid falling for the scam.
Phone calls
Tech support scammers often call and pretend to be a computer technician from a well-known company. They say they’ve found a problem with your computer. They typically ask you to give them remote access to your computer and then pretend to run a diagnostic test. Then they try to make you pay to fix a problem that doesn’t exist. Listen to an FTC undercover call with a tech support scammer.
If you get a phone call you didn’t expect from someone who says there’s a problem with your computer, hang up.
Pop-up warnings
Tech support scammers may try to trick you with a pop-up window that appears on your computer screen. It might look like an error message from your operating system or antivirus software, and it might use logos from trusted companies or websites. The message in the window warns you about a security issue on your computer and tells you to call a phone number to get help.
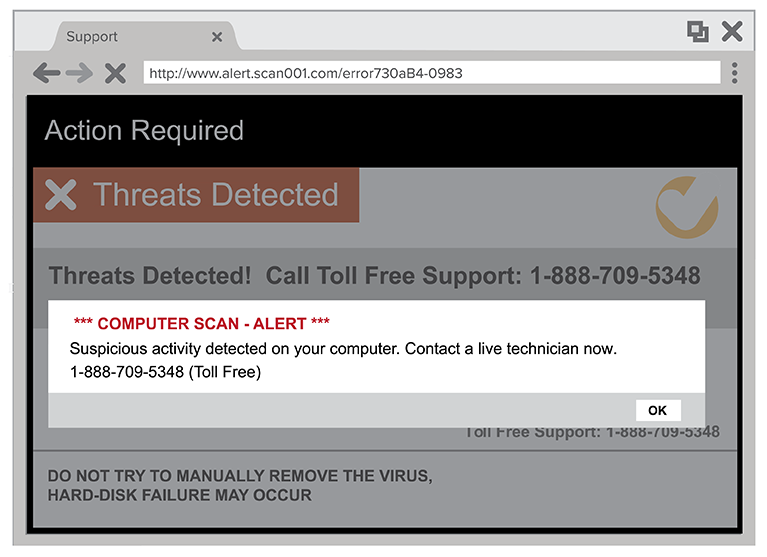
If you get this kind of pop-up window on your computer, don’t call the number.
Real security warnings and messages will never ask you to call a phone number.
Online ads and listings in search results pages
Tech support scammers try to get their websites to show up in online search results for tech support. Or they might run their own ads online. The scammers are hoping you’ll call the phone number to get help.
If you’re looking for tech support, go to a company you know and trust.
Two Things To Know To Avoid a Tech Support Scam
- Legitimate tech companies won’t contact you by phone, email, or text message to tell you there’s a problem with your computer.
- Security pop-up warnings from real tech companies will never ask you to call a phone number or click on a link.
What To Do if You Think There’s a Problem With Your Computer
If you think there may be a problem with your computer, update your computer’s security software and run a scan.
If you need help fixing a problem, go to someone you know and trust. Many software companies offer support online or by phone. Stores that sell computer equipment also offer technical support in person.
What To Do if You Were Scammed
If you paid a tech support scammer with a credit or debit card, you may be able to stop the transaction. Contact your credit card company or bank right away. Tell them what happened and ask if they can reverse the charges.
If you paid a tech support scammer with a gift card, contact the company that issued the card right away. Tell them you paid a scammer with the gift card and ask if they can refund your money.
If you gave a scammer remote access to your computer, update your computer’s security software. Then run a scan and delete anything it identifies as a problem.
If you gave your username and password to a tech support scammer, change your password right away. If you use the same password for other accounts or sites, change it there, too. Create a new password that is strong.
Avoid Tech Support Refund Scams
If someone calls to offer you a refund for tech support services you paid for, it’s likely a fake refund scam. How does the scam work? The caller will ask if you were happy with the services you got. If you say, “No,” they’ll offer you a refund. In another variation, the caller says the company is giving out refunds because it’s going out of business. No matter their story, they’re not giving refunds. They’re trying to steal more of your money. Don’t give them your bank account, credit card, or other payment information.
Reporting Tech Support Scams
If a tech support scammer contacts you, report it to the FTC at ReportFraud.ftc.gov.
When you report a scam, the FTC uses the information to build cases against scammers. Now that you know how to recognize a tech support scam, share what you learned with someone you know. You might help them avoid a tech support scam.
